圆月山庄资源网 Design By www.vgjia.com
原文链接:https://www.52pojie.cn/thread-1608459-1-1.html
一、准备工作
目标软件是一个加了VMP并开启虚拟化及代码变异,脱壳过程略,直接看脱壳的结果
11.png
可以看到关键地方全部被虚拟化了,关于虚拟化处理起来我还没有很好的解决方案
二、去除反调试
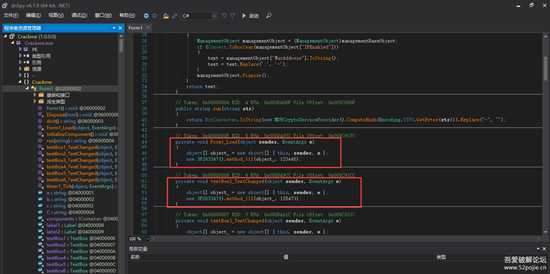
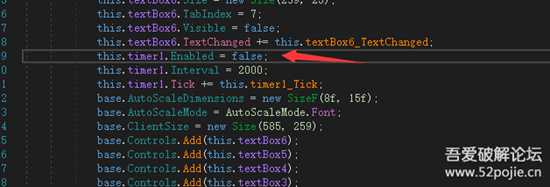
timer1里有进程检测反调试,每2秒检测是否包含{“dnSpy”,“de4dot”,“64”,“32”,“ExtremeDumper”}字样,将timer1时钟设置为flase即可关闭检测
22.png
de4dot直接修改会清除vmp区段,这里我直接跳转到16禁止去c32修改的,将0xC98F6这里修改为0就可以啦

33.png
三、追码
解决反调试后我找了个软件来帮助解决虚拟化代码的问题,下面贴软件生成的log
[Asm] 纯文本查看 复制代码
2022-03-23 13:19:42.639 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.639 +08:00 [WRN] {2022-03-23 13:19:42.640 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.640 +08:00 [VRB] MethodName: Replace2022-03-23 13:19:42.640 +08:00 [VRB] FullDescription: System.String System.String::Replace(System.String oldValue, System.String newValue)2022-03-23 13:19:42.640 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.640 +08:00 [VRB] Obj: "D93D3311D3NN2C9D213DC21DR1QD9234"2022-03-23 13:19:42.640 +08:00 [VRB] Parameter (System.String) [0]: ("0")2022-03-23 13:19:42.640 +08:00 [VRB] Parameter (System.String) [1]: ("D")2022-03-23 13:19:42.641 +08:00 [VRB] MDToken: 0x60005422022-03-23 13:19:42.641 +08:00 [VRB] Return Type: System.String2022-03-23 13:19:42.641 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.641 +08:00 [VRB] Returns: D93D3311D3NN2C9D213DC21DR1QD92342022-03-23 13:19:42.641 +08:00 [WRN] }2022-03-23 13:19:42.641 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.641 +08:00 [WRN] {2022-03-23 13:19:42.641 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.641 +08:00 [VRB] MethodName: Replace2022-03-23 13:19:42.641 +08:00 [VRB] FullDescription: System.String System.String::Replace(System.String oldValue, System.String newValue)2022-03-23 13:19:42.641 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.641 +08:00 [VRB] Obj: "D93D3311D3NN2C9D213DC21DR1QD9234"2022-03-23 13:19:42.641 +08:00 [VRB] Parameter (System.String) [0]: ("8")2022-03-23 13:19:42.641 +08:00 [VRB] Parameter (System.String) [1]: ("C")2022-03-23 13:19:42.641 +08:00 [VRB] MDToken: 0x60005422022-03-23 13:19:42.642 +08:00 [VRB] Return Type: System.String2022-03-23 13:19:42.642 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.642 +08:00 [VRB] Returns: D93D3311D3NN2C9D213DC21DR1QD92342022-03-23 13:19:42.642 +08:00 [WRN] }2022-03-23 13:19:42.642 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.642 +08:00 [WRN] {2022-03-23 13:19:42.642 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.642 +08:00 [VRB] MethodName: Replace2022-03-23 13:19:42.642 +08:00 [VRB] FullDescription: System.String System.String::Replace(System.String oldValue, System.String newValue)2022-03-23 13:19:42.643 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.643 +08:00 [VRB] Obj: "D93D3311D3NN2C9D213DC21DR1QD9234"2022-03-23 13:19:42.643 +08:00 [VRB] Parameter (System.String) [0]: ("7")2022-03-23 13:19:42.643 +08:00 [VRB] Parameter (System.String) [1]: ("N")2022-03-23 13:19:42.643 +08:00 [VRB] MDToken: 0x60005422022-03-23 13:19:42.643 +08:00 [VRB] Return Type: System.String2022-03-23 13:19:42.643 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.643 +08:00 [VRB] Returns: D93D3311D3NN2C9D213DC21DR1QD92342022-03-23 13:19:42.643 +08:00 [WRN] }2022-03-23 13:19:42.643 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.643 +08:00 [WRN] {2022-03-23 13:19:42.643 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.643 +08:00 [VRB] MethodName: Replace2022-03-23 13:19:42.643 +08:00 [VRB] FullDescription: System.String System.String::Replace(System.String oldValue, System.String newValue)2022-03-23 13:19:42.643 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.643 +08:00 [VRB] Obj: "D93D3311D3NN2C9D213DC21DR1QD9234"2022-03-23 13:19:42.644 +08:00 [VRB] Parameter (System.String) [0]: ("5")2022-03-23 13:19:42.644 +08:00 [VRB] Parameter (System.String) [1]: ("Q")2022-03-23 13:19:42.644 +08:00 [VRB] MDToken: 0x60005422022-03-23 13:19:42.644 +08:00 [VRB] Return Type: System.String2022-03-23 13:19:42.644 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.644 +08:00 [VRB] Returns: D93D3311D3NN2C9D213DC21DR1QD92342022-03-23 13:19:42.644 +08:00 [WRN] }2022-03-23 13:19:42.644 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.644 +08:00 [WRN] {2022-03-23 13:19:42.644 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.644 +08:00 [VRB] MethodName: Replace2022-03-23 13:19:42.644 +08:00 [VRB] FullDescription: System.String System.String::Replace(System.String oldValue, System.String newValue)2022-03-23 13:19:42.644 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.644 +08:00 [VRB] Obj: "D93D3311D3NN2C9D213DC21DR1QD9234"2022-03-23 13:19:42.644 +08:00 [VRB] Parameter (System.String) [0]: ("6")2022-03-23 13:19:42.645 +08:00 [VRB] Parameter (System.String) [1]: ("R")2022-03-23 13:19:42.645 +08:00 [VRB] MDToken: 0x60005422022-03-23 13:19:42.645 +08:00 [VRB] Return Type: System.String2022-03-23 13:19:42.645 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.645 +08:00 [VRB] Returns: D93D3311D3NN2C9D213DC21DR1QD92342022-03-23 13:19:42.645 +08:00 [WRN] }2022-03-23 13:19:42.645 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.645 +08:00 [WRN] {2022-03-23 13:19:42.645 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.645 +08:00 [VRB] MethodName: Replace2022-03-23 13:19:42.645 +08:00 [VRB] FullDescription: System.String System.String::Replace(System.String oldValue, System.String newValue)2022-03-23 13:19:42.645 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.645 +08:00 [VRB] Obj: "D93D3311D3NN2C9D213DC21DR1QD9234"2022-03-23 13:19:42.645 +08:00 [VRB] Parameter (System.String) [0]: ("L")2022-03-23 13:19:42.645 +08:00 [VRB] Parameter (System.String) [1]: ("4")2022-03-23 13:19:42.646 +08:00 [VRB] MDToken: 0x60005422022-03-23 13:19:42.646 +08:00 [VRB] Return Type: System.String2022-03-23 13:19:42.646 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.646 +08:00 [VRB] Returns: D93D3311D3NN2C9D213DC21DR1QD92342022-03-23 13:19:42.646 +08:00 [WRN] }2022-03-23 13:19:42.646 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.646 +08:00 [WRN] {2022-03-23 13:19:42.646 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.646 +08:00 [VRB] MethodName: Replace2022-03-23 13:19:42.646 +08:00 [VRB] FullDescription: System.String System.String::Replace(System.String oldValue, System.String newValue)2022-03-23 13:19:42.646 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.646 +08:00 [VRB] Obj: "D93D3311D3NN2C9D213DC21DR1QD9234"2022-03-23 13:19:42.646 +08:00 [VRB] Parameter (System.String) [0]: ("A")2022-03-23 13:19:42.646 +08:00 [VRB] Parameter (System.String) [1]: ("2")2022-03-23 13:19:42.646 +08:00 [VRB] MDToken: 0x60005422022-03-23 13:19:42.647 +08:00 [VRB] Return Type: System.String2022-03-23 13:19:42.647 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.647 +08:00 [VRB] Returns: D93D3311D3NN2C9D213DC21DR1QD92342022-03-23 13:19:42.647 +08:00 [WRN] }2022-03-23 13:19:42.647 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.647 +08:00 [WRN] {2022-03-23 13:19:42.647 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.647 +08:00 [VRB] MethodName: Replace2022-03-23 13:19:42.647 +08:00 [VRB] FullDescription: System.String System.String::Replace(System.String oldValue, System.String newValue)2022-03-23 13:19:42.647 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.647 +08:00 [VRB] Obj: "D93D3311D3NN2C9D213DC21DR1QD9234"2022-03-23 13:19:42.647 +08:00 [VRB] Parameter (System.String) [0]: ("B")2022-03-23 13:19:42.647 +08:00 [VRB] Parameter (System.String) [1]: ("3")2022-03-23 13:19:42.647 +08:00 [VRB] MDToken: 0x60005422022-03-23 13:19:42.647 +08:00 [VRB] Return Type: System.String2022-03-23 13:19:42.648 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.648 +08:00 [VRB] Returns: D93D3311D3NN2C9D213DC21DR1QD92342022-03-23 13:19:42.648 +08:00 [WRN] }2022-03-23 13:19:42.648 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.648 +08:00 [WRN] {2022-03-23 13:19:42.648 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.648 +08:00 [VRB] MethodName: Replace2022-03-23 13:19:42.648 +08:00 [VRB] FullDescription: System.String System.String::Replace(System.String oldValue, System.String newValue)2022-03-23 13:19:42.648 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.648 +08:00 [VRB] Obj: "D93D3311D3NN2C9D213DC21DR1QD9234"2022-03-23 13:19:42.648 +08:00 [VRB] Parameter (System.String) [0]: ("E")2022-03-23 13:19:42.648 +08:00 [VRB] Parameter (System.String) [1]: ("0")2022-03-23 13:19:42.648 +08:00 [VRB] MDToken: 0x60005422022-03-23 13:19:42.648 +08:00 [VRB] Return Type: System.String2022-03-23 13:19:42.649 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.649 +08:00 [VRB] Returns: D93D3311D3NN2C9D213DC21DR1QD92342022-03-23 13:19:42.649 +08:00 [WRN] }2022-03-23 13:19:42.649 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.649 +08:00 [WRN] {2022-03-23 13:19:42.649 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.649 +08:00 [VRB] MethodName: Replace2022-03-23 13:19:42.649 +08:00 [VRB] FullDescription: System.String System.String::Replace(System.String oldValue, System.String newValue)2022-03-23 13:19:42.649 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.649 +08:00 [VRB] Obj: "D93D3311D3NN2C9D213DC21DR1QD9234"2022-03-23 13:19:42.649 +08:00 [VRB] Parameter (System.String) [0]: ("F")2022-03-23 13:19:42.649 +08:00 [VRB] Parameter (System.String) [1]: ("1")2022-03-23 13:19:42.649 +08:00 [VRB] MDToken: 0x60005422022-03-23 13:19:42.649 +08:00 [VRB] Return Type: System.String2022-03-23 13:19:42.649 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.650 +08:00 [VRB] Returns: D93D3311D3NN2C9D213DC21DR1QD92342022-03-23 13:19:42.650 +08:00 [WRN] }2022-03-23 13:19:42.650 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.650 +08:00 [WRN] {2022-03-23 13:19:42.650 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.650 +08:00 [VRB] MethodName: Replace2022-03-23 13:19:42.650 +08:00 [VRB] FullDescription: System.String System.String::Replace(System.String oldValue, System.String newValue)2022-03-23 13:19:42.650 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.650 +08:00 [VRB] Obj: "D93D3311D3NN2C9D213DC21DR1QD9234"2022-03-23 13:19:42.650 +08:00 [VRB] Parameter (System.String) [0]: ("M")2022-03-23 13:19:42.650 +08:00 [VRB] Parameter (System.String) [1]: ("9")2022-03-23 13:19:42.651 +08:00 [VRB] MDToken: 0x60005422022-03-23 13:19:42.651 +08:00 [VRB] Return Type: System.String2022-03-23 13:19:42.651 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.651 +08:00 [VRB] Returns: D93D3311D3NN2C9D213DC21DR1QD92342022-03-23 13:19:42.651 +08:00 [WRN] }2022-03-23 13:19:42.651 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.651 +08:00 [WRN] {2022-03-23 13:19:42.651 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.651 +08:00 [VRB] MethodName: ToArray2022-03-23 13:19:42.651 +08:00 [VRB] FullDescription: static System.Char[] System.Linq.Enumerable::ToArray(System.Collections.Generic.IEnumerable`1<System.Char> source)2022-03-23 13:19:42.651 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.651 +08:00 [VRB] Parameter (System.String) [0]: ("D93D3311D3NN2C9D213DC21DR1QD9234")2022-03-23 13:19:42.651 +08:00 [VRB] MDToken: 0x6000B6F2022-03-23 13:19:42.651 +08:00 [VRB] Return Type: System.Char[]2022-03-23 13:19:42.652 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.652 +08:00 [VRB] Returns: ["D","9","3","D","3","3","1","1","D","3","N","N","2","C","9","D","2","1","3","D","C","2","1","D","R","1","Q","D","9","2","3","4"]2022-03-23 13:19:42.652 +08:00 [WRN] }2022-03-23 13:19:42.652 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.652 +08:00 [WRN] {2022-03-23 13:19:42.652 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.652 +08:00 [VRB] MethodName: get_Length2022-03-23 13:19:42.652 +08:00 [VRB] FullDescription: System.Int32 System.String::get_Length()2022-03-23 13:19:42.652 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.652 +08:00 [VRB] Obj: "D93D3311D3NN2C9D213DC21DR1QD9234"2022-03-23 13:19:42.653 +08:00 [VRB] MDToken: 0x60004D22022-03-23 13:19:42.653 +08:00 [VRB] Return Type: System.Int322022-03-23 13:19:42.653 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.653 +08:00 [VRB] Returns: 322022-03-23 13:19:42.653 +08:00 [WRN] }2022-03-23 13:19:42.653 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.653 +08:00 [WRN] {2022-03-23 13:19:42.653 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.653 +08:00 [VRB] MethodName: smethod_02022-03-23 13:19:42.653 +08:00 [VRB] FullDescription: static System.Void 7B4E5853::smethod_0(System.Array array_0, System.Int32 int_0, System.Int32 int_1)2022-03-23 13:19:42.653 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.653 +08:00 [VRB] Parameter (System.Char[]) [0]: (Char[] {D, 9, 3, D, 3, 3, 1, 1, D, 3, N, N, 2, C, 9, D, 2, 1, 3, D, C, 2, 1, D, R, 1, Q, D, 9, 2, 3, 4})2022-03-23 13:19:42.653 +08:00 [VRB] Parameter (System.Int32) [1]: (0)2022-03-23 13:19:42.653 +08:00 [VRB] Parameter (System.Int32) [2]: (32)2022-03-23 13:19:42.654 +08:00 [VRB] MDToken: 0x60000942022-03-23 13:19:42.654 +08:00 [VRB] Return Type: System.Void2022-03-23 13:19:42.654 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.654 +08:00 [VRB] Returns: null2022-03-23 13:19:42.654 +08:00 [WRN] }2022-03-23 13:19:42.654 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.654 +08:00 [WRN] {2022-03-23 13:19:42.654 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.654 +08:00 [VRB] MethodName: smethod_02022-03-23 13:19:42.654 +08:00 [VRB] FullDescription: static System.Object 37891AB0::smethod_0()2022-03-23 13:19:42.654 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.654 +08:00 [VRB] MDToken: 0x60000492022-03-23 13:19:42.654 +08:00 [VRB] Return Type: System.Object2022-03-23 13:19:42.654 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.654 +08:00 [VRB] Returns: 2022-03-23 13:19:42.655 +08:00 [WRN] }2022-03-23 13:19:42.657 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.657 +08:00 [WRN] {2022-03-23 13:19:42.657 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.657 +08:00 [VRB] MethodName: smethod_02022-03-23 13:19:42.657 +08:00 [VRB] FullDescription: static System.Text.StringBuilder 1C814297::smethod_0(System.Object object_0, System.Char[] char_0)2022-03-23 13:19:42.657 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.658 +08:00 [VRB] Parameter (System.Text.StringBuilder) [0]: ()2022-03-23 13:19:42.658 +08:00 [VRB] Parameter (System.Char[]) [1]: (Char[] {4, 3, 2, 9, D, Q, 1, R, D, 1, 2, C, D, 3, 1, 2, D, 9, C, 2, N, N, 3, D, 1, 1, 3, 3, D, 3, 9, D})2022-03-23 13:19:42.658 +08:00 [VRB] MDToken: 0x60000402022-03-23 13:19:42.658 +08:00 [VRB] Return Type: System.Text.StringBuilder2022-03-23 13:19:42.658 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.658 +08:00 [VRB] Returns: 4329DQ1RD12CD312D9C2NN3D1133D39D2022-03-23 13:19:42.658 +08:00 [WRN] }2022-03-23 13:19:42.658 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.658 +08:00 [WRN] {2022-03-23 13:19:42.659 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.659 +08:00 [VRB] MethodName: ToString2022-03-23 13:19:42.659 +08:00 [VRB] FullDescription: virtual System.String System.Object::ToString()2022-03-23 13:19:42.659 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.659 +08:00 [VRB] Obj: 4329DQ1RD12CD312D9C2NN3D1133D39D2022-03-23 13:19:42.659 +08:00 [VRB] MDToken: 0x600022A2022-03-23 13:19:42.659 +08:00 [VRB] Return Type: System.String2022-03-23 13:19:42.659 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.659 +08:00 [VRB] Returns: 4329DQ1RD12CD312D9C2NN3D1133D39D2022-03-23 13:19:42.659 +08:00 [WRN] }2022-03-23 13:19:42.659 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.659 +08:00 [WRN] {2022-03-23 13:19:42.659 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.660 +08:00 [VRB] MethodName: smethod_02022-03-23 13:19:42.660 +08:00 [VRB] FullDescription: static System.String 680A5711::smethod_0(System.Object object_0)2022-03-23 13:19:42.660 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.660 +08:00 [VRB] Parameter (System.Windows.Forms.TextBox) [0]: (System.Windows.Forms.TextBox, Text: 1245)2022-03-23 13:19:42.660 +08:00 [VRB] MDToken: 0x60000222022-03-23 13:19:42.660 +08:00 [VRB] Return Type: System.String2022-03-23 13:19:42.660 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.660 +08:00 [VRB] Returns: 12452022-03-23 13:19:42.660 +08:00 [WRN] }2022-03-23 13:19:42.660 +08:00 [INF] VmProtectDumperUnsafeInvoke Prefix:2022-03-23 13:19:42.660 +08:00 [WRN] {2022-03-23 13:19:42.660 +08:00 [VRB] VMP MethodName: System.Void Crackme.Form1::textBox2_TextChanged(System.Object sender, System.EventArgs e) (MDToken 0x100663302)2022-03-23 13:19:42.660 +08:00 [VRB] MethodName: smethod_02022-03-23 13:19:42.660 +08:00 [VRB] FullDescription: static System.Boolean 094923F6::smethod_0(System.String string_0, System.String string_1)2022-03-23 13:19:42.661 +08:00 [VRB] MethodType: System.Reflection.RuntimeMethodInfo2022-03-23 13:19:42.661 +08:00 [VRB] Parameter (System.String) [0]: ("1245")2022-03-23 13:19:42.661 +08:00 [VRB] Parameter (System.String) [1]: ("4329DQ1RD12CD312D9C2NN3D1133D39D")2022-03-23 13:19:42.661 +08:00 [VRB] MDToken: 0x600003A2022-03-23 13:19:42.661 +08:00 [VRB] Return Type: System.Boolean2022-03-23 13:19:42.661 +08:00 [INF] VmProtectDumperUnsafeInvoke Result:2022-03-23 13:19:42.661 +08:00 [VRB] Returns: false2022-03-23 13:19:42.661 +08:00 [WRN] }
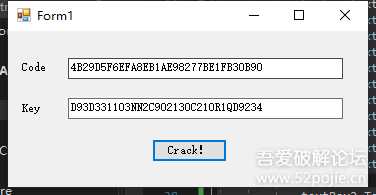
我的机器码为4B29D5F6EFA8EB1AE98277BE1FB30B90,此时正确的key为D93D3311D3NN2C9D213DC21DR1QD9234
44.png
四、分析算法
借助于软件的log分析起来应该不难,直接贴注册机成品算法了
首先是机器码的算法
[C#] 纯文本查看 复制代码
public string doIt() { string text = null; foreach (ManagementBaseObject managementBaseObject in new ManagementClass("Win32_NetworkAdapterConfiguration").GetInstances()) { ManagementObject managementObject = (ManagementObject)managementBaseObject; if (Convert.ToBoolean(managementObject["IPEnabled"])) { text = managementObject["MacAddress"].ToString(); text = text.Replace(':', '-'); } managementObject.Dispose(); } return text; } public string run(string str) { return BitConverter.ToString(new MD5CryptoServiceProvider().ComputeHash(Encoding.UTF8.GetBytes(str))).Replace("-", ""); } private void Form1_Load(object sender, EventArgs e) { textBox1.Text = run(doIt().Replace("-", "")); }
下面是注册机的算法
[C#] 纯文本查看 复制代码
private void button1_Click(object sender, EventArgs e) { string text; text = textBox1.Text.Replace("0","D"); text = text.Replace("8", "C"); text = text.Replace("7", "N"); text = text.Replace("5", "Q"); text = text.Replace("6", "R"); text = text.Replace("L", "4"); text = text.Replace("A", "2"); text = text.Replace("B", "3"); text = text.Replace("E", "0"); text = text.Replace("F", "1"); text = text.Replace("M", "9"); textBox2.Text = ReverseA(text); } public string ReverseA(string text) { char[] cArray = text.ToCharArray(); string reverse = String.Empty; for (int i = cArray.Length - 1; i > -1; i--) { reverse += cArray[i]; } return reverse; }
完活@Domado
标签:
分析一个.NET CM
圆月山庄资源网 Design By www.vgjia.com
广告合作:本站广告合作请联系QQ:858582 申请时备注:广告合作(否则不回)
免责声明:本站文章均来自网站采集或用户投稿,网站不提供任何软件下载或自行开发的软件! 如有用户或公司发现本站内容信息存在侵权行为,请邮件告知! 858582#qq.com
免责声明:本站文章均来自网站采集或用户投稿,网站不提供任何软件下载或自行开发的软件! 如有用户或公司发现本站内容信息存在侵权行为,请邮件告知! 858582#qq.com
圆月山庄资源网 Design By www.vgjia.com
暂无评论...
《魔兽世界》大逃杀!60人新游玩模式《强袭风暴》3月21日上线
暴雪近日发布了《魔兽世界》10.2.6 更新内容,新游玩模式《强袭风暴》即将于3月21 日在亚服上线,届时玩家将前往阿拉希高地展开一场 60 人大逃杀对战。
艾泽拉斯的冒险者已经征服了艾泽拉斯的大地及遥远的彼岸。他们在对抗世界上最致命的敌人时展现出过人的手腕,并且成功阻止终结宇宙等级的威胁。当他们在为即将于《魔兽世界》资料片《地心之战》中来袭的萨拉塔斯势力做战斗准备时,他们还需要在熟悉的阿拉希高地面对一个全新的敌人──那就是彼此。在《巨龙崛起》10.2.6 更新的《强袭风暴》中,玩家将会进入一个全新的海盗主题大逃杀式限时活动,其中包含极高的风险和史诗级的奖励。
《强袭风暴》不是普通的战场,作为一个独立于主游戏之外的活动,玩家可以用大逃杀的风格来体验《魔兽世界》,不分职业、不分装备(除了你在赛局中捡到的),光是技巧和战略的强弱之分就能决定出谁才是能坚持到最后的赢家。本次活动将会开放单人和双人模式,玩家在加入海盗主题的预赛大厅区域前,可以从强袭风暴角色画面新增好友。游玩游戏将可以累计名望轨迹,《巨龙崛起》和《魔兽世界:巫妖王之怒 经典版》的玩家都可以获得奖励。
更新日志
2025年01月12日
2025年01月12日
- 小骆驼-《草原狼2(蓝光CD)》[原抓WAV+CUE]
- 群星《欢迎来到我身边 电影原声专辑》[320K/MP3][105.02MB]
- 群星《欢迎来到我身边 电影原声专辑》[FLAC/分轨][480.9MB]
- 雷婷《梦里蓝天HQⅡ》 2023头版限量编号低速原抓[WAV+CUE][463M]
- 群星《2024好听新歌42》AI调整音效【WAV分轨】
- 王思雨-《思念陪着鸿雁飞》WAV
- 王思雨《喜马拉雅HQ》头版限量编号[WAV+CUE]
- 李健《无时无刻》[WAV+CUE][590M]
- 陈奕迅《酝酿》[WAV分轨][502M]
- 卓依婷《化蝶》2CD[WAV+CUE][1.1G]
- 群星《吉他王(黑胶CD)》[WAV+CUE]
- 齐秦《穿乐(穿越)》[WAV+CUE]
- 发烧珍品《数位CD音响测试-动向效果(九)》【WAV+CUE】
- 邝美云《邝美云精装歌集》[DSF][1.6G]
- 吕方《爱一回伤一回》[WAV+CUE][454M]
